The purpose of a modern phone is of course communication: not only via the cell radio, but over the internet.
Naturally, this is a vital tool for the user. But the predominance of always-on network connectivity has lead to increasing abuse by providers of phone software: both Google and other creators of the operating system, and third-party app creators. As far as they are concerned, the phone’s true purpose is to (i) gather information about their users and (ii) serve advertising back at them based on this information.
Both these functions – antithetical to the users needs and wishes – rely on the internet. The baleful combination became possible with the rise of widespread mobile internet. In this post we’ll take control back over our network functions, so only the components we says can ever send or receive data on our phone. After all, we pay for it!
Firewall
AFWall+
With a rooted phone, a low-level firewall can be used to ensure only exactly specified processes can send or receive data over the internet. This is possible because Android is linux-based, and includes the long-standing iptables firewall built-in.
I recommend AFWall+ as a firewall frontend. On a rooted machine it’s easy to install – you can get it on F-Droid here.
It’s easy to configure as well. By default you can turn off all data access across all processes. Then you can allow individual application internet access over wireless, radio, roaming etc. This is useful for preventing apps from eating your precious roaming data – e.g. only doing updates over a wifi connection.
Once you’ve got a set of rules, remember to go Settings -> Apply to apply them to the firewall!
Limiting Core and System access
With user apps, you can be very strict – if you never use them to access the internet, feel free to deny them access completely.
For the core and system, there are some components that need to have access to allow core functions (like wifi calling) to work properly. You can see these in the Core and System filters in AFWall+.
I’ve put a list of the minimal permissions you need to get full phone functionality on the Qin F21 Pro:
Core:
- Linux Kernel
- Multicast DNS
- Media Server
- Internet Time servers
- (root) Apps running as root
- (tethering) DHCP+DNS services
System (each is one service):
- Download Manager, Downloads, MTP host, Sounds,
com.android.providers.media - GBA Service, Phone and Messaging Storage, Telephone Assist, MmsService
- Mobile anti-theft, Dynamic System Updates, Android System
- Network manager, Cell Broadcast Service, Tethering
- microG services core
Turning them off won’t have a catastrophic effect – but you’ll lose connectivity.
Boot anti-leak
The AFWall only starts and sets firewall rules once the phone is booted. This means there is potentially a brief window where applications can slip in and access the internet without your permission.
A Magisk module exists that is specifically designed to prevent this “leak”. It’s called AFWall Boot AntiLeak by GrayJackFixxxer.
Find it in the Magisk Modules Alt Repo in MMM, or get it directly from source here.
Connectivity Leaks
DNS
The DNS (domain name system) is a very basic part of the internet that resolves readable domain names like jonayling.net to IP addresses. Anything that accesses the internet uses a DNS to resolve hostnames.
The unfortunate thing about this is that whoever runs the DNS can gather a lot of information about what sites you visit. The good news is there are lots of DNS servers out there which work identically and may even be faster than your default DNS.
To stop Google hoovering up this data, we can really easily change DNS using a dedicated Magisk module. I’m currently using CloudflareDNS4Magisk v2.7 by Rom. This will switch to using Cloudflare as your DNS. You can access it in the Alt Magisk Module repository in MMM.
Captive Portal Check
(For more details see Mike Kekutz’s blog posts on this [in German]).
Did you know that Android phones connect to a Google server every time you first access the internet? The reason for this is the Captive Portal Check. A “Captive Portal” is an internet network where some sort of browser-based login is required to use it (like in a hotel, for instance). The captive portal check checks connectivity by trying to contact Google’s server’s – if it can’t it redirects you to the logon page.
I don’t know about you, but I hardly use captive portal internet at all. I’m therefore not keen on Google being pinged every time I use the internet.
Fortunately, it’s easy to either (i) turn off the captive portal check or (ii) redirect it to use a different server. You’ll need the adb tool and a rooted device.
To turn it off, open a rooted shell on your device (using adb with it plugged in with USB debugging) and execute:
adb shell
adb su
settings put global captive_portal_detection_enabled 0
settings put global captive_portal_mode 0
settings put global captive_portal_server localhostAlternatively, you can repoint the captive portal check to another test URL, like captiveportal.kuketz.de (this is run by the internet security expert Mike Kuketz and will not harvest any of your data). Run the following in a root shell:
settings put global captive_portal_http_url "http://captiveportal.kuketz.de"
settings put global captive_portal_https_url "https://captiveportal.kuketz.de"
settings put global captive_portal_fallback_url "http://captiveportal.kuketz.de"
settings put global captive_portal_other_fallback_urls "http://captiveportal.kuketz.de"Ad-blocking
Ad blocking is really fundamental to taking control back over our devices and not being used by them as tools. As the main place where revenue is extracted, it’s the end goal of the whole mobile attention ecosystem. Since we’re going to turn that back around to our advantage, my philosophy is scorched earth here: I won’t tolerate any advertisements whatsoever (I’ll happily pay for good content).
Because Android is linux-based, there exists a powerful and universal way to block remote content you don’t like (including adverts): the hosts file. This is a (fairly ancient) bit of linux that overrides the DNS mechanism we talked about earlier – meaning you can add domains you don’t like to it and make sure they never “resolve” (i.e. reach the internet).
On rooted phones, Android ad-blockers use the hosts file to prevent adverts from loading from known advertising servers. The lists are hand-curated and (very actively) maintained – it’s all easy and automatic. And you’ll never see an ad on your phone – in an app or the browser – again.
A good ad-blocking solution is AdAway. You can get this from F-Droid here.
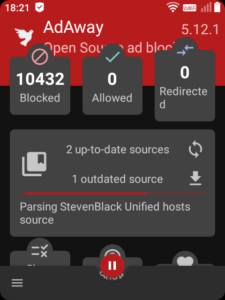
You can sign up to various block lists: Pete Lowe‘s and Steven Black‘s are very thorough and actively maintained. Then just activate it and away you go!